
Snowflake object naming conventions
A Snowflake object naming convention is a framework for naming objects in a way that describes what they contain and how …

Federated authentication enables your users to connect to Snowflake using secure SSO (single sign-on). With SSO enabled, your users authenticate through an external, SAML 2.0-compliant identity provider (IdP). In this article we will see how to configure Google Workspace as an identity provider for Snowflake SSO.
Unlike SCIM(System for Cross-domain Identity Management) integration with Okta and Azure, automatic provisioning with Google Workspace does not work in Snowflake. Therefore you will have to manually create your users in Snowflake, if this is a requirement you should consider using either Okta OR Azure SCIM Integration with Snowflake as of the writing of this document.
The next set of instructions assumes you have access to the Google Workspace admin console to configure Snowflake as an application.
Log into Google Admin console for your Google Workspace account
Navigate to Apps –> Web and mobile apps –> Add app –> Add custom SAML app
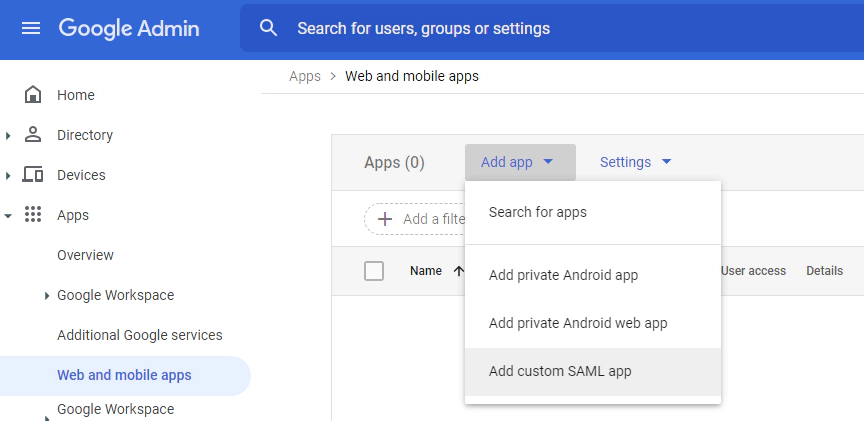
Enter the name of the application and upload a snowflake logo. Uploading the logo is not mandatory, but it gives a good UI
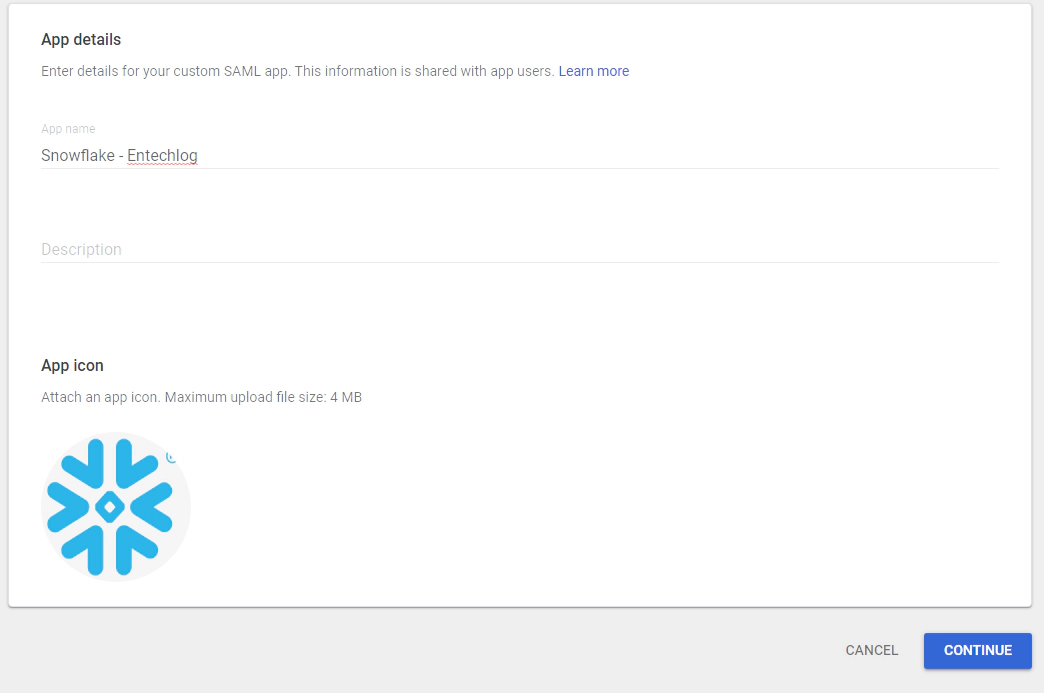
Click on download idP metadata and keep the information safe, this will be required in next steps
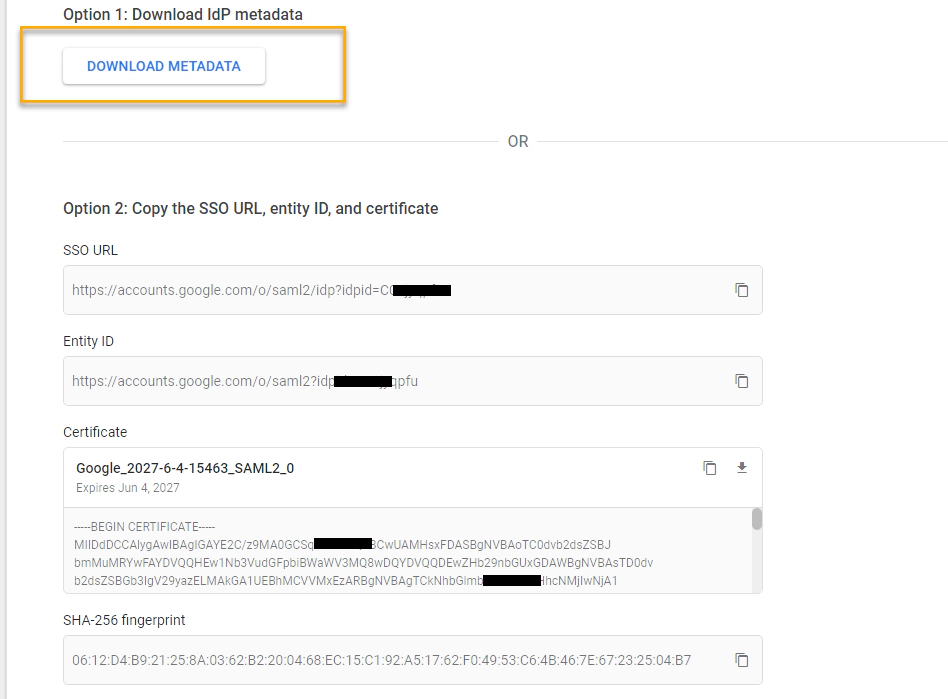
Fill the service provider details, In this case the service provider is Snowflake with ACS URL, Entity ID, Name ID format, Name ID.
ACS URL: https://[ACCOUNT].[region].snowflakecomputing.com/fed/login
Entity ID: https://[ACCOUNT].[region].snowflakecomputing.com
Name ID format: EMAIL
Name ID: Basic Information > Primary email
Make sure ACCOUNT is always in upper case and with Snowflake region-less URL region is not required.
You should already have this information, but can be also retrieved by running the query.
select t.value:type::varchar as type,
t.value:host::varchar as host,
t.value:port as port
from table(flatten(input => parse_json(system$whitelist()))) as t
WHERE type = 'SNOWFLAKE_DEPLOYMENT';
Click “Finish” on this page to complete adding the SAML app. Since this process can’t auto provision users and groups, the group mapping here adds no value.
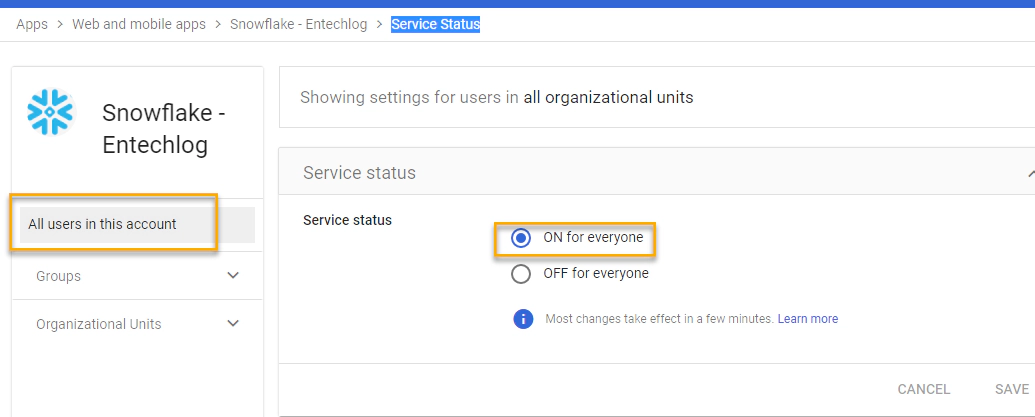
Navigate to “Apps > Web and mobile apps > Snowflake - Entechlog > Service Status”, click on “All users in the account” and turn on the service status for all users
Login into Snowflake as account admin
Update below sql with certificate, issuer and ssoUrl information from idP metadata XML and execute the query to setup the SAML_IDENTITY_PROVIDER
certificate content should be in single line with no spaces OR newline
use role accountadmin;
alter account set SAML_IDENTITY_PROVIDER =
'{
"certificate": "MII...WxO",
"issuer": "https://accounts.google.com/o/saml2?idpid=Cxxxxxxx",
"ssoUrl": "https://accounts.google.com/o/saml2/idp?idpid=Cxxxxxxx",
"type" : "custom",
"label" : "GoogleSSO"
}';
alter account set sso_login_page = true;
Add users to snowflake. This can be done manually using below sql OR using terraform
CREATE USER "example@entechlog.com";
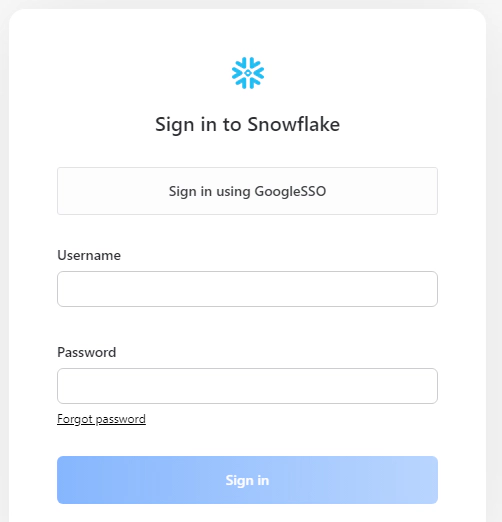
Navigate to the login URL for your account and click “Sign in using GoogleSSO”. This should authenticate into Snowflake if the integration has no errors in the setup.
Snowflake recently announced that using security integration is preferred over SCIM. SCIM can be easily migrated into security integration by running the below queries
Show existing security integrations, This should show the existing SCIM integration details
SHOW SECURITY INTEGRATIONS;
Run the migration query using SYSTEM$MIGRATE_SAML_IDP_REGISTRATION( ‘<integration_name>’, ‘<issuer>’ )
SELECT SYSTEM$MIGRATE_SAML_IDP_REGISTRATION( 'GoogleSSO', 'https://accounts.google.com/o/saml2?idpid=Cxxxxxxx')
Successful migration will give the query result “SUCCESS : [GOOGLESSO] Fed SAML Integration created”
Describe the security integration for Google SSO
SHOW SECURITY INTEGRATIONS;
DESC SECURITY INTEGRATION GOOGLESSO;
Hope this was helpful. Did I miss something ? Let me know in the comments.
This blog represents my own viewpoints and not of my employer, Snowflake. All product names, logos, and brands are the property of their respective owners.

A Snowflake object naming convention is a framework for naming objects in a way that describes what they contain and how …
Snowpipe is Snowflake’s continuous data ingestion service. Snowpipe loads data within minutes after files are …